Protect What?
Need to do formal assessment:
- Identify the information assets that need protecting
- Describe the architecture of the information system to be deployed
Typical Architecture
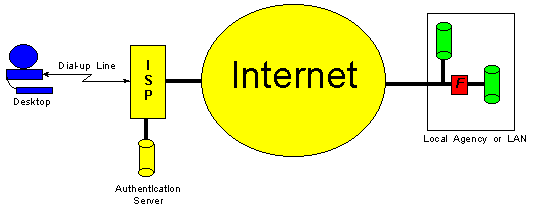
| |
- Identify and rank the threats to those information assets based on the architecture
- Identify the most serious threats and develop solutions to mitigate the threats as much as possible
- Make specific recommendations of solutions for deployment

 Copyright © 1998 HLN Consulting LLC (http://www.hln.com/)
Copyright © 1998 HLN Consulting LLC (http://www.hln.com/)



 Copyright © 1998 HLN Consulting LLC (http://www.hln.com/)
Copyright © 1998 HLN Consulting LLC (http://www.hln.com/)