- Develop an information security policy that delineates the roles and responsibilities of the Program staff and participants (including the "public")
- Systems and operations training, including backup personnel.
- Consulting assistance needs to be provided when necessary.
- Server should be kept in a locked facility, alarmed whenever left unattended
- Uninterrupted power
- Data backups (including off-site storage of backup media), including restoration from backups tested periodically
- Isolate Web server functions; only run necessary processes
- Be careful of poorly-designed CGI programs, server-side includes, and applets
- Audit systems; look at logs!
- Consider relative security of different platforms, and functionality tradeoffs that are often inversely related to security
- Consider outsourcing server operations to minimize the exposure of rest of the network
- Domain restriction offers some protection, especially when used in conjunction with a properly-configured firewall
- Password protection of web pages provides very limited security; use a separate namespace where possible
- Encrypt data stream where possible (e.g., SSL)
- IP subnet upon which the server is attached should be a "trusted" subnet: all computers on the subnet should be used and administered by "trusted" personnel.
- Consider emerging virtual private networks
| Virtual Private Network using L2TP |
|---|
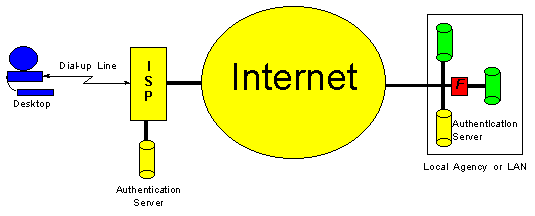
|

 Copyright © 1998 HLN Consulting LLC (http://www.hln.com/)
Copyright © 1998 HLN Consulting LLC (http://www.hln.com/)